Kaspersky CTF – help (Forensic 500)
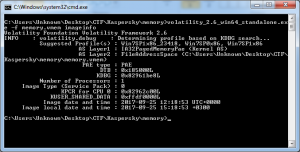
We were given a memory dump; First we’ll get image info to understand the image type:
It is Windows 7 x64. As usual we check running processes to find possible suspicious ones:
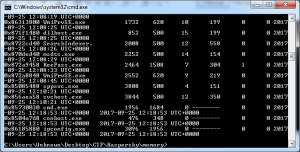
There are only two suspect processes: ‘Keepass.exe’ and ‘Cmd.exe’; The first one interested me more and probably I should try to find ‘kdbx’ or ‘kdb’ file, so I scanned for file lists to get something to start:
Yes, it is. Let’s dump it. It should be a known password like something inside ‘rockyou.txt’ or even numeric. I used my favorite password cracker to break it. It wasn’t in ‘rockyou.txt’. Then I checked for digits and again nothing! Hex range characters! No luck! Lower case letters! No luck! Really?!
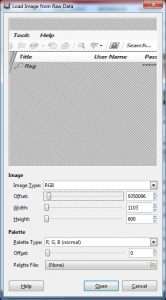
So, what now? I thought maybe ‘KeePass’ has the flag as entire title so I dumped memory of ‘Keepass.exe’ and started looking at the memory as raw image in Gimp, definitely the worst decision, it took about 2 hours to get a clear shot and I wasted my time:
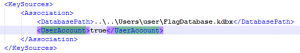
The flag was not the title and I had to crack AES256 hence I had no idea about password format or charsets. I looked at ‘KeePass.config.xml’ and understood it used ‘Windows Account’ as authentication:
OK, probably it has to be tricks or ‘Keepass’ vulnerability, I Googled and got some useful information:
` It may be possible to recover a KeePass database whose Master Key includes a Windows User Account (WUA) if certain user data is available`
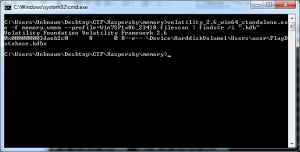
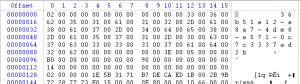
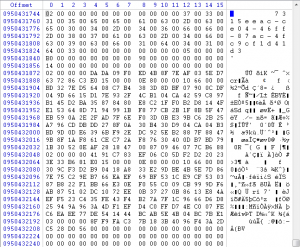
So I had to follow the routines step by step to open the database. At first, I thought I have to find the user password (I still don’t know is it needed or not) but I tried any techniques I could think of: mimikatz (failed), hashdump and then try to crack (failed), and the last one was ‘lsadump’ which works and I found the password, it was ‘you_need_another_key_to_pass_this_level’. The Computer Name was ‘WIN-GFCKT3R8MQ2’, Domain was ‘WORKGROUP’ also I have ‘ProtectedUserKey.bin’; But something’s missing and that was master key and it was important to recover the master key. I tried so many times to dump it ‘\Device\HarddiskVolume1\Users\user\AppData\Roaming\Microsoft\Protect\S-1-5-21-196189514-4237867838-3788442389-1000\7315eeac-ce04-46ff-87ac-4fc9cf1d41d3’ but it failed, so I tried some abnormal way, built a database and used its header to find the master key in memory:
After I found this way the rest was simple, I had all I needed:
So, I imitated my machine with all I had, and now I had to use ‘DPAPI migration.reg’ Which I will refer to at the end of the post, and finally ‘c:\windows\system32\dpapimig.exe’…. And…..
Failed!!
WTF!!
OK, I did that… And….
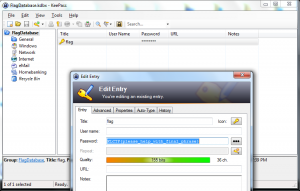
YEEESSS! It works!! First blood on Kaspersky’s forensic challenge.
It was too much fun and tricky but I spent about 12 hours to solve this task. If you’re reading the article and you laugh because now the secrets revealed and I was blind on all steps and it was completely trial and error. This is it!
Reference: https://sourceforge.net/p/keepass/wiki/Recover Windows User Account Credentials/
Ghaaf @ irGeeks
Hi Ghaaf,
I was stuck on this problem. I really appreciate for your writeup. May I know how do you dump the KeePass.config.xml from filescan?
Thanks,
Johnny
Sorry, I just can’t understand how you dump the master key “\Device\HarddiskVolume1\Users\user\AppData\Roaming\Microsoft\Protect\S-1-5-21-196189514-4237867838-3788442389-1000\7315eeac-ce04-46ff-87ac-4fc9cf1d41d3”.
can you explain it explicitly?
Thank you very much!
Good Job ! Really nice write-up.
Is it possible to get the memory dump please ?
Excellent , As Always